
Backup Validation
Many organizations only discover corrupted or malware-infected backups during a crisis, when its far too late. Realize true recovery assurance with AI-powered Backup Validation, featuring cleanroom-based threat scanning, automated testing, and recoverability scoring.
-
Service
OverviewMost backup tools confirm your data was “saved”. What they can’t confirm is whether that data is clean, bootable, and recoverable. Dormant ransomware can silently infiltrate your backups, leaving you with no clean recovery point when you need it most. This blind spot is the Cyber Recovery Gap, and closing it is critical to your cyber resiliency strategy.
Recovery Point’s Backup Validation Service transforms your backups from untested assumptions into proven recovery assurance. By continually validating backups in an isolated cleanroom environment, we help ensure your systems are not only backed up but recoverable, malware-free, and operational. Unlike standard tools, our fully managed service combines:
- Automated system-level recovery testing
- Advanced threat scanning for dormant or embedded malware
- Recoverability scoring and proof of resilience you can share with auditors, insurers, and executives
Benefits
-

Assured Recovery
Minimize downtime risk by validating that systems can be restored quickly and effectively after ransomware or a disaster.
-

Audit-Ready Proof
Simplify compliance, cyber insurance, and executive reporting with structured, automated validation reports.
-

Risk Reduction Without Complexity
Close the Cyber Recovery Gap without costly rip-and-replace. Our service seamlessly integrates with your existing backup tools and workflows.
-

Operational Efficiency
Reduce IT overhead with fully managed, automated recovery testing that frees staff from manual processes.
-

Intelligent Threat Detection
Identify dormant or embedded malware that bypasses traditional XDR/EDR tools, ensuring you have a clean recovery point.
-

Proactive Cyber Resilience
Continual validation delivers proactive resilience that turns backups into a reliable core layer of your cybersecurity defense strategy.
Cyber Recovery Readiness Assessment
Are your backups actually recoverable? Self-assess whether your backup and recovery strategy can withstand a real-world ransomware attack with our quick survey.
Stats
Backups are no longer a guaranteed safety net. Attackers now target backup systems directly, and too many organizations discover too late that their data can’t be recovered. These stats highlight why validated, provable recoverability is essential to cyber resilience.
-
93 %
of ransomware attacks now target backup infrastructure itself, making secure storage alone insufficient.
-
75 %
of companies faced failed backup recoveries after a cyberattack.
-
41 %
of companies that paid a ransom still failed to recover all their data.

-
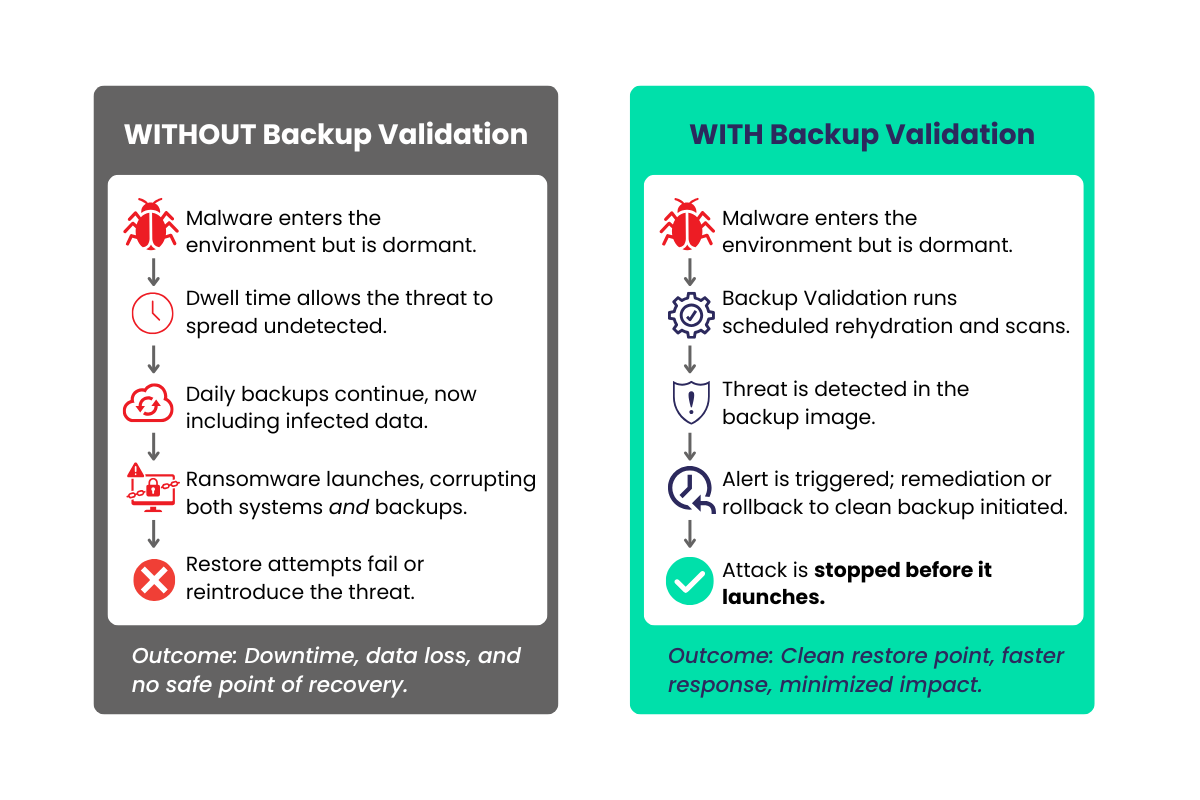 The Cyber Recovery Gap in Action
The Cyber Recovery Gap in ActionAnatomy of an Attack
Ransomware often spreads quietly, slipping into backups long before it detonates. What look like safe recovery points are already compromised, leaving restores to fail or reintroduce malware when it matters most.
Backup Validation changes that outcome. Backups are rehydrated and scanned in a secure cleanroom to catch threats early, trigger remediation, and provide a trusted path to fast, clean recovery.
How Backup Validation Works
1. Rehydrate backups in a safe, isolated cleanroom
Backups are automatically restored on schedule into a secure cleanroom to simulate real recovery.
2. Power on and test systems for real-world recoverability
Systems are booted and verified to ensure they start and function as expected – beyond just data integrity checks.
3. Scan for hidden malware and anomalies
Integrated malware and anomaly scans identify threats missed by production XDR/EDR tools.
4. Score and report on your recovery readiness
Quantifiable insights show the health and recoverability of your backups, delivering structured outputs for audit, regulatory, and cyber insurance needs.

Schedule a Free Consultation
Reach out today to start a conversation on how to harness predictive and proactive strategies to ensure you stay ahead of the next generation of disruptions.
Backup Validation - Contact Form
"*" indicates required fields



