The New Normal in Disaster Recovery: Preparing for Ransomware Attacks Takes a New Approach
Automation, Backup, Business Continuity, Cleanroom, Cybersecurity, Data Protection, Disaster Recovery, Managed Services, Ransomware


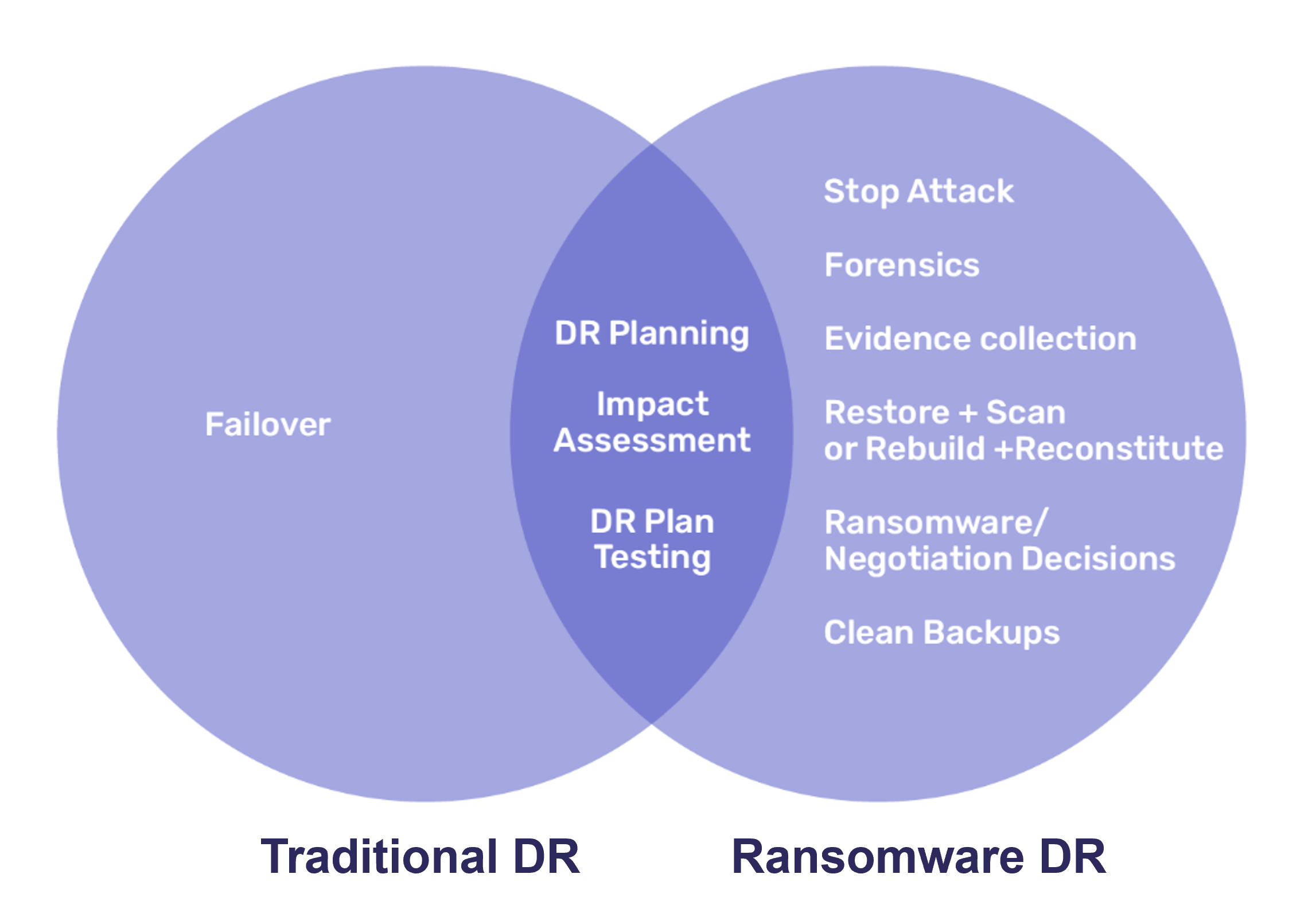
While many organizations have established Disaster Recovery (DR) plans for traditional threats like natural disasters, hardware failures, or human errors, the unique nature of ransomware attacks requires a distinct approach to recovery. Ransomware attacks often have a broader and more unpredictable impact. They require immediate action to contain the threat and mitigate damage, and can corrupt or encrypt backup data, complicating the recovery process.
Ransomware recovery also often involves coordination across multiple departments and may use different techniques and tools than traditional DR scenarios. Organizations must recognize these distinctions to develop comprehensive, effective strategies that go beyond traditional DR planning and ensure business continuity and data protection against evolving cyber threats.
Traditional Disaster Recovery
Disaster Recovery in the standard context refers to the policies, tools, and procedures designed to recover vital technology infrastructure and systems after a major outage. It primarily focuses on restoring IT operations at an alternate site if the primary site becomes unavailable. DR plans address various scenarios, from hurricanes, floods, and power failures to physical damage to facilities and human mistakes. The key components of traditional DR include:
- Backups and restoration processes
- Data replication and offsite storage
- Comprehensive disaster recovery planning and testing
- Defining Recovery Time Objective (RTO) and Recovery Point Objective (RPO) metrics
With regular data backups, real-time or near-real-time data replication to secondary locations, and offsite storage to protect against localized disasters, data can be restored quickly and securely with minimal disruption.
Traditional DR is part of a broader Business Continuity Planning (BCP) process which identifies critical business functions and their supporting IT systems, establishes alternate work locations, ensures continuity of essential services and supply chains, and trains staff on DR procedures.
Ransomware Recovery
A ransomware attack occurs when malicious actors encrypt an organization’s data and demand payment for its release. Recovering from an encryption attack presents unique challenges, including data integrity issues, time pressure, and legal implications. Ransomware attackers use various methods to infiltrate systems, such as phishing emails, exploiting vulnerabilities, and social engineering tactics.
Importantly, ransomware can severely impact traditional backup and recovery strategies by encrypting or corrupting backup files, compromising backup software, and potentially affecting disaster recovery sites. Hence, immediate response to a ransomware attack is critical. This includes:
- Containment and mitigation efforts such as isolating affected systems
- Disabling network services that could facilitate spread
- Implementing network segmentation
- Engaging incident response teams
It’s also vital to rapidly determine the extent of the attack by identifying compromised systems and accounts, determining the specific ransomware variant, investigating the entry point, and assessing the impact on critical business functions and data.
These factors demand a more dynamic, multi-faceted approach when compared to traditional disaster recovery. It requires not only technical expertise in data recovery but also skills in threat analysis, cybersecurity, and crisis management.
Key Differences
- Predictability: Because traditional DR often deals with foreseeable scenarios like natural disasters or hardware failures, they allow for advanced risk assessment and rehearsed recovery processes. In contrast, ransomware recovery faces highly unpredictable attacks with continuously evolving tactics, requiring adaptable recovery processes to deal with unknown variables.
- Response Time: Traditional DR follows pre-defined, step-by-step recovery plans with scheduled failovers and manageable timelines. In ransomware recovery, the luxury of a planned failover is absent, as the focus is on containing the threat while simultaneously initiating recovery efforts.
- Scope: Traditional DR typically affects specific locations or systems, with clearly defined impacts and recovery focused on pre-identified critical systems. Ransomware attacks can rapidly spread across entire networks, potentially affecting multiple systems and locations enterprise-wide. This widespread impact necessitates addressing a vast and complex ecosystem of affected systems during recovery.
The Challenge
Early detection of ransomware can be difficult due to sophisticated malware that operates stealthily, attacks occurring outside business hours, and the scale of large, complex networks. Rapid containment prevents further spread but requires quick decision-making to isolate systems without disrupting critical operations. Tracing the initial point of entry and identifying all compromised systems is complex and time-consuming but essential to prevent reinfection.
Isolated Recovery Environments (IREs) or Cleanrooms provide secure, isolated environments for data recovery and system rebuilding, designed to prevent reinfection during the recovery process. However, implementing IREs comes with its own challenges such as ensuring true isolation, balancing isolation with access to recovery resources, and scaling capacity to handle enterprise-wide recovery efforts. Operational complexities include securely transferring and validating data, managing access controls, and coordinating recovery efforts across multiple teams in a restricted environment.
Best Practices
Given the scale, sophistication, and frequency of ransomware attacks today, no organization can afford to assume their systems and data are uncompromisable, even if protected by robust cybersecurity protocols, including multi-layered security defenses, strong access controls, and network segmentation.
To protect against data loss, organizations of all types need to implement immutable and air-gapped backups using write-once-read-many (WORM) technology and physically or logically isolating backup systems from the main network. Increasing backup frequency and redundancy is also advised, along with diversifying backup storage and maintaining multiple versions of backups with appropriate retention policies.
Incident response planning is another key aspect. Regular testing and updating of ransomware-specific playbooks and plans through tabletop exercises and full-scale simulations can be very helpful. Employee training on recognizing and reporting suspicious activities, such as phishing attempts and social engineering tactics, is also a useful framework for building a culture of security awareness.
The Ransomware Recovery Solution
Recovery Point offers Ransomware Recovery as a Service (RRaaS) to help organizations address the growing threat of ransomware attacks. The service goes beyond traditional disaster recovery offerings by providing proactive preparation, secure and accelerated recovery, and ongoing resilience.
Key benefits include:
- Deployment flexibility and multi-platform support
- Enhanced data integrity through immutable backups and regular scanning
- WORM backups and IRE cleanroom operations
- Rapid recovery with automated processes and hot site failover
- Expert guidance from experienced data recovery specialists
At the heart of the offering is Recovery Point’s proprietary Resiliency Management Platform (RMP), which enables automation and orchestration, centralized management, scalability, customization, integration capabilities, and continuous improvement through built-in analytics and regular updates to address emerging threats and incorporate new recovery technologies.
The threat of ransomware is only growing. Ensure your recovery process is prepared for it.
Recovery Point specializes in complete recovery solutions purpose-built to respond to today’s most advanced cyber threats like ransomware. Contact us today to learn how we can protect your organization.
Contact us to connect with our team now.
Connect with us on LinkedIn, X (formerly Twitter), and Facebook.
